There is at least one patient data breach every day!
Patient records are in danger! And the biggest threat comes from inadequate privacy and security measures used by healthcare providers and their IT vendors.
One of the important ways to protect your patients’ data and save yourself from devastating penalties and lawsuits is to build a HIPAA-compliant electronic medical records system.
In this article, we are going to show you 7 key elements of HIPAA compliance for electronic records that will help you protect your patient data.
But we’ll start by getting some important definitions out of the way: What is EHR? How is it different from EMR? And what do they have to do with HIPAA? Read on to find out, or if you are already an expert, skip ahead to the compliance steps.
EHR and EMR Systems: Meaning & Difference
Both EHR and EMR stand for electronic patient records, and therefore, people often use them as synonymous. So why change one damn letter and confuse people, you ask?
Because these are not the same systems. EMR is a system that a particular healthcare provider uses to collect and track all patient data in his or her facility. Thus, patient data in EMRs is limited to a single provider. EHRs, on the other hand, accumulate data across different healthcare providers and specialists involved in taking care of the patient.
Despite the fact that these systems are different, the general HIPAA compliance requirements for them are pretty much the same. So forgive us for sounding like amateurs, but for the purposes of this article, we are still going to use these terms interchangeably.
Benefits of Having EHRs and EMRs
The two systems also have a lot in common in terms of the benefits they bring to medical practices and clinics. Although, since EHRs are more extensive, they can be more beneficial both for patients and providers.
The key benefits of EHRs and EMRs include:
- Tracking patient data over time
- Reminders for repeated tasks (e.g. checkups, medical procedures)
- Automated appointment scheduling
- Automated shift scheduling
Since EHRs collect all data from all providers, their benefits also include:
- Helping doctors in decision making, by providing full medical data
- Automatic lab test ordering
- ePrescriptions
- And much more
Therefore, when implemented correctly, you will find either of the systems will be beneficial to your practice. Now, let’s see what EMRs and EHRs have to do with HIPAA.
HIPAA and EHR: Why Should They Go Together?
The Health Insurance Portability and Accountability Act (HIPAA) is a US legislation that protects patient information.
You have to be concerned with HIPAA if you are a covered entity, i.e. you collect patient information to provide healthcare services and bill insurance.
The information that you are obliged to keep secure is called Protected Healthcare Information (PHI) when it is in physical records or Electronic Protected Healthcare Information (ePHI) when it is in digital form. This information includes demographics, medical history, mental health information, lab results, insurance information, all of which is coupled with personally identifiable information (e.g. name, social security number, address). So basically, everything you keep in your EHR/EMR.
Your EMR or EHR is going to harbor all the electronic information that you have to protect by law. That is why you need to account for all the technical requirements when developing a custom EMR or, in case you choose to buy an off-the-shelf system, make sure it complies with this law.
Most of the compliance requirements for EMRs are listed in the Technical Safeguards of the Security Rule of HIPAA. We’ve compiled them into the 7 key elements of EMR compliance and listed them below for your convenience.
But before that, let’s talk about some scary stuff: What is going to happen if you don’t comply?
What are the Dangers of Your EMR/EHR Not Complying with HIPAA?
Besides the moral implications of not treating your patients’ data fairly, there are other more tangible consequences. These range in severity, from not getting a monetary incentive to fully blown disasters — like a gazillion-dollar lawsuit. Let’s talk about them in ascending order of severity…
- ‘Meaningful Use’ Incentives
If you are eligible for either Medicare or Medicaid incentive programs (‘Meaningful Use’), your EHR has to meet a long list of criteria to get it. Providing privacy and security are in that list too, thus, a lot of requirements intersect with HIPAA. If you don’t comply, you won’t be able to get the incentives.
- Electronic Medical Records and HIPAA violations
A very important thing to keep in mind here is that HIPAA doesn’t penalize you for breaches, but rather for noncompliance. Therefore, in theory, if you thoroughly cover the ground with all HIPAA requirements, but somebody still manages to hack you, you won’t get fined.
However, if you don’t comply, HHS can penalize you for violations even if there is no breach! Someone can report a violation, or you can be subject to a random audit.
HIPAA penalties range from $100 to $1.5 million per violation.
- Lawsuits
When a breach occurs, under HIPAA you are legally obligated to notify all patients whose data has been compromised, and in some cases, even the media.
As a result, patients whose data have been compromised may want to sue you.
Below, we are mentioning a disastrous case where patients from 12 states combined their efforts to sue an EHR vendor!
Now, how is that for motivation to build a HIPAA compliant EMR?!
How to Keep Your Electronic Health Records Safe and Comply with HIPAA
HIPAA and electronic medical records remain such a mystery to many people because there is no all-encompassing ultimate checklist. HHS was very careful not to be too specific, as the issue of security is very complex and technology is changing so rapidly that no single checklist could accommodate it all.
But fear not — we’ve put together a list of the key aspects that will help you get started.

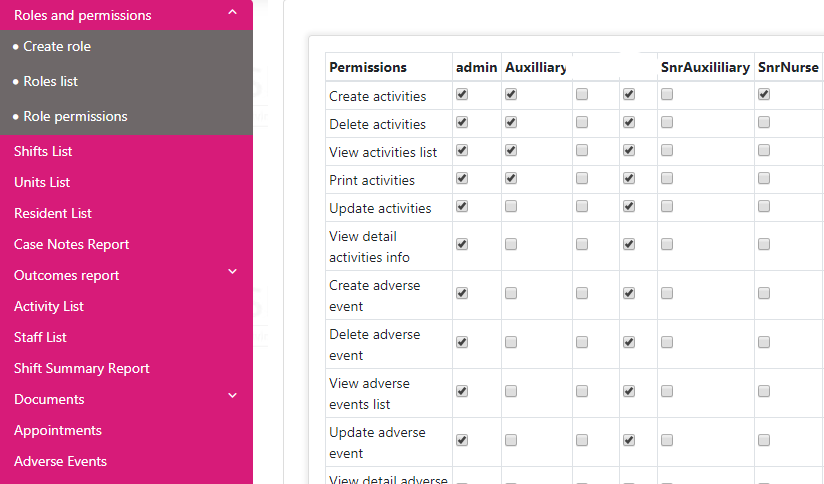
Authorization
Who gets access to what information? You have to be very careful and deliberate about this.
The Administrative Safeguards section of the Security Rule states that you need to:
“Implement procedures for the authorization and/or supervision of workforce members who work with electronic protected health information or in locations where it might be accessed.” AUTHORIZATION AND/OR SUPERVISION (A) – (§ 164.308(a)(3)(ii)(A))
Thus, it is important to make sure that your employees only get access to the information they absolutely need and nothing more (the Minimum Necessary rule). For instance, an X-ray specialist only needs to see data related to the procedure they are about to perform, e.g. past related injuries. However, the specialist doesn’t need to see the entire medical history or all personally identifiable information, like a patient’s address or phone number.
In addition to deciding what patient data each user can see, you should also determine what each user can and cannot do with that data. This is also part of the HIPAA requirements, and it is referred to as a standard called ‘Integrity’ stated in the Technical Safeguards (§ 164.312(c)(1)). This standard says that you should protect the data from being improperly changed or deleted.
To ensure this, you need to establish different access levels for different user roles in your EMR. Once you’ve identified the rights and privileges of each employee regarding patient information, you can configure your EMR to reflect that. This will also mean that some employees will get some parts of ePHI in ‘read-only’ mode.
2. Authentication
Every time a user logs into your EMR, you have to make sure that this user is who he says he is. This is called ‘authentication’. Only after the system authenticates the user can he/she get access to ePHI with the rights and permissions that you determined previously for this person.
“Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.” § 164.312(d)
The Security Rule outlines three types of authentication:
- Password or PIN code
- A unique item that a user possesses, like a security key, token, or a code
- Biometrics like fingerprints, voice patterns, facial patterns, etc.
Although passwords are the easiest and the most common ways of authentication, they are also less reliable. That is why HHS recommends considering using other forms of authentication.
Also, don’t forget to store your user and system credentials securely. Writing EMR passwords on sticky notes and attaching them to computer screens is hardly HIPAA compliant. Instead, consider using a specialized credential management system like AWS Secrets Manager.
Another good idea would be to use temporary user credentials that expire after a certain period of time and have to be replaced with new ones.
To illustrate the severity of the matter, consider this famous case…
Medical Informatics Engineering (MIE), an EHR vendor, failed to follow the basic authentication requirements and created shared accounts for testing. Several employees were sharing the same login ‘tester’ and password ‘testing’ to get access to the system. No unique user identification was required. Hackers used this account to explore the vulnerabilities of the system. As a result, they managed to attack the system several times, compromising millions of patient records at 11 hospitals that used this system. Besides the authentication, MIE also had other HIPAA violations, such as not encrypting sensitive data, not providing proper personnel training, no risk assessment, etc. This made the job of hackers even easier. The consequences of this negligence were dear. Not only did they have to pay $100,000 for HIPAA violations, but they also had to deal with the first-ever EHR-related lawsuit from 12 states.
3. Automatic Logoff
To prevent unauthorized access, your employees should always log off once they leave their workstation (any device on which they use EMR). However, since we’re only humans, the chances that one of the users will forget to do it are high. That is why it is best to implement an automatic logoff in your EMR so that a session is terminated automatically after a certain period of time when the system is not used.
“Implement electronic procedures that terminate an electronic session after a predetermined time of inactivity.” § 164.312(a)(2)(iii)
Only you can determine what time it should be — 5, 10, or more minutes — so that it is both secure and convenient for your personnel. Once you’ve defined the appropriate time for session termination, you or your developers can configure your EMR accordingly.
4. Audits and Alerts
You need to know about any violation or breach as soon as it occurs so that you could take timely measures. How is this possible? With audits and alerts.
“Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information.” § 164.312(b)
You can only protect ePHI if you know what happens to it at all times: who accesses it, what actions a user performs, and if he/she is authorized to do it. That is why your EMR should have an audit trail functionality that automatically logs each user activity all the time.
Of course, it is not enough to just log everything, you need to be able to use this information to prevent or stop violations as soon as they occur. For that you need to:
- Regularly review your audit logs (Section §164.310(a)(1)(ii)(D) of the Security Rule)
- Set up automated alerts for any suspicious activity, like unauthorized access.
Here is an example of what can happen if you don’t implement audit controls in your EMR, even if you do everything else right:
Memorial Healthcare System (MHS), a nonprofit healthcare provider, had to pay $5.5 million for violations that resulted in impermissible access to patient information. Its employees used the account credentials of a former employee to get access and share information of 115,143 patients. Although MHS had the proper information access policies in place, the employees chose not to follow them and the company didn’t have the tools to find out about it right away. Because MHS didn’t have audit controls, they discovered this violation only after a year!
5. Encryption
HIPAA states that you need to encrypt your patient information whenever it is at high risk.
“Implement a mechanism to encrypt electronic protected health information whenever deemed appropriate.” § 164.312(e)(2)(ii)
The requirement is addressable, which means that it is up to you to decide if you need to encrypt data at all, and if you do, what parts and when. Even though encryption is not mandatory, you still need to have very good reasons not to do it, which also have to be documented. This documentation will come in handy in case of a breach or a violation, such as, for example, a theft of a computer with ePHI on it.
Data transmission is considered one of the highest risk situations, and HHS advises you to encrypt your data whenever you send your patient data via email or transfer it from your EMR to another system.
However, both Amazon and Google agree that it’s better to be safe than sorry and require data encryption both in transit and at rest. So if you decide to use AWS or Google cloud hosting for your EMR, not encrypting your data will violate your Business Associate Agreement (which you have to sign with the cloud vendor you choose — we will cover this in more detail later).
Another risky situation is when you or your employees access ePHI from their portable devices (smartphones, tablets, laptops, or USB sticks). Out of all healthcare breaches, 10% are attributed to loss and theft of physical devices containing ePHI.
Taxes Cancer Center is one of the most notorious cases in this regard. Within one year, one of its employees had his laptop stolen and another lost two USB drives with unencrypted ePHI. These devices contained records of 33,500 patients. This resulted in $4.3 million of HIPAA penalties for the series of violations that led to these incidents.
6. HIPAA Compliant Hosting and Infrastructure
If you build your own custom EHR system, you need to decide where it is going to be hosted and make sure that the hosting is compliant.
A HIPAA compliant ePHI storage and infrastructure means that the data has to be protected in every way possible:
- Physically securing servers with doors, locks, video surveillance, alarms, etc.
- Administratively by strictly controlling access to servers and introducing appropriate policies and procedures for the personnel
- Technically by providing server software security, as well as reliable backup and recovery
Depending on the hosting option you choose, either you will be the only one to bear all of these security responsibilities (and costs) or you’ll share them with your service providers (Business Associates).
Your hosting options are as follows:
- On-premise: your EHR/EMR will be stored on your own servers at your location.
- Cloud-based: when your system and ePHI is are stored on a cloud service such as Google Cloud or Amazon Cloud.
- Platform as a Service: a variation of the cloud-based storage, and in this case, your ePHI will be stored at a third-party platform.

The first option of hosting everything on your own hardware at your own location will bring you the most liabilities and costs. You will have to make sure that your servers are in the best shape at all times by constantly monitoring them and fixing/upgrading whenever needed. You will be responsible for reliable backups and accommodating big user loads in cases where a lot of users access your system at the same time.
The alternative to this is storing everything on a HIPAA-compliant cloud. As we’ve already mentioned, both Google and Amazon provide compliant cloud services, as well as some other vendors. With this approach, you can reap the benefits of using state-of-the-art server security and infrastructure created by thousands of top minds in the industry. In addition to that, you can save money too. Both of these cloud giants operate at an incredible scale which makes their services very cost-efficient. They offer ‘pay only for what you use’ pricing, so you are paying only for the storage capacity and services that you’ve actually used in a month.
With this approach, you share the responsibility to protect patient data with the cloud services provider of your choice. Basically, they will be responsible for the physical protection of the servers and providing all the necessary services and features for securely storing data, but it will be your responsibility to configure and use them properly. The responsibilities of both sides are outlined in the Business Associate Addendum (BAA) that you will need to sign with your vendor.
There is another option — to transfer all data storage responsibilities to your vendor. For example, TrueVault is a solution for HIPAA compliant data storage that your web development team can use to build HIPAA compliant EHR. TrueVault will be responsible for storing your data in a HIPAA compliant and secure manner so you or your team don’t have to deal with it. To work with TrueVault, you also have to sign the BAA with them that will outline both their and your responsibilities for HIPAA compliance.
All of that sounds nice, but how do you know which one is better for your project? To answer this question, your software development team will have to analyze all of the requirements of your system. There is no one solution that will fit everyone perfectly.
Have trouble deciding on the hosting solution? Hire us to prepare a Business Analysis for your EHR!
Contact Us7. Business Associate Addendum
A Business Associate Addendum or BAA is a contract that you sign with any third-party service provider that is going to have access to your patients' protected information.
BAAs are very important in regard to HIPAA and medical records because they make everyone involved in ePHI handling responsible.

You need to sign these contracts with service providers, referred to as Business Associates in this case. They are any contractors, vendors, or freelancers, i.e. organizations or people who are not members of your workforce. Here are some examples of Business Associates who may have access to your ePHI:
- Cloud hosting providers or data storage solution providers (e.g. Google or Amazon or TrueVault)
- Web development teams that you hire to develop your own custom EHR
- EHR vendors, if you consider using an off-the-shelf solution.
Here are some key points that the BAA should cover:
- How the data is going to be used by your Business Associate
- How your partner is not going to use or disclose the ePHI in any other way that is not specified in the contract
- What safeguards your partner is going to implement to protect your data
- How your associate has to report to you about any misuse or breach as soon as possible
- How your partner is going to destroy or dispose of the ePHI in case you terminate your contract
How to Apply This To Your Practice
We hope that this article gives you an overview of the EMR and HIPAA relationship.
Let’s recap the key elements we covered. A compliant EMR or EHR allows only authorized data access, automatically terminates sessions during periods of inactivity, audits all user activity and sends alerts whenever anything suspicious happens, encrypts data (especially in risky situations), and is hosted at HIPAA compliant servers and infrastructure. In addition to that, you need to sign a BAA with any vendor or service provider who will have access to the patient data.
Now you see that EMR and HIPAA compliance is not rocket science, but it does take a serious approach and a set of deliberate choices. One of those choices involves choosing the right web development team.
Now that you’re up to speed on HIPAA requirements, we’d like to shamelessly ask you to consider our team. We have experience in developing secure EHR systems for different healthcare providers, from psychotherapy practice to assisted living facilities. Our team specializes in developing custom-tailored software from scratch that fits the exact requirements of our clients.
Let's talk about the development of a custom EHR that fits 100% of your needs!
Contact UsRate this article!
5
 PHP Development
PHP Development Laravel
Laravel Yii
Yii





Comments (0)